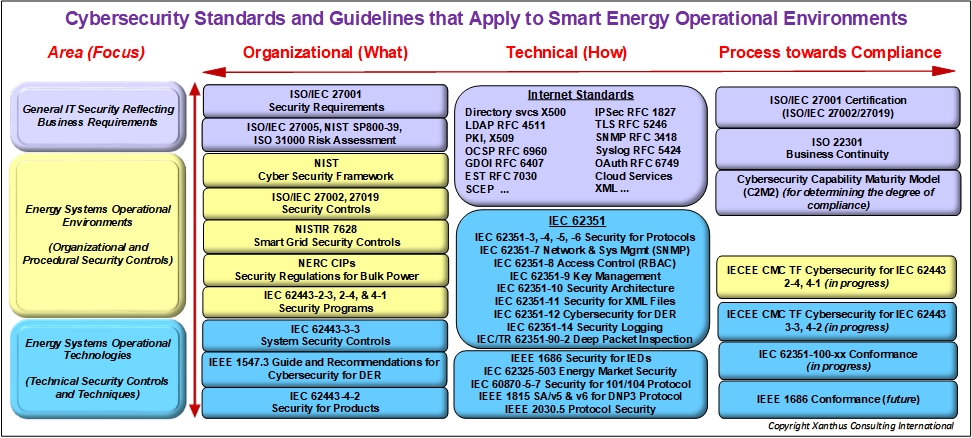
IEC 62351 Standards: Cybersecurity for IEC 61850, IEC 60870-5 (101/104 and DNP3), IEC 60870-6 (ICCP), and IEC 61968/61970 (CIM)
The IEC 62351 series of standards include cybersecurity technologies for the communication protocols defined by the IEC TC 57, specifically the IEC 60870-5 series (including IEEE 1815 (DNP3) as a derivative standard), the IEC 60870-6 series, the IEC 61850 series, the IEC 61970 series, and the IEC 61968 series. As shown in the figure below, there is not a one-to-one correlation between the IEC TC57 communication protocol standards and the IEC 62351 security standards. This is because many of the communication protocols rely on the same underlying cybersecurity standards at different layers.
The IEC 62351 series also defines the cybersecurity requirements for implementing security technologies in the operational environment, including objects for network and system management (e.g. with SNMP), role-based access control (RBAC), cryptographic key management, and security event logging.
Technical specifications for conformance testing, applicable for these standards, are also being developed as part of this series as IEC/TS 62351-100-xx.
IEC 62351 standards profile the use of existing Internet standards whenever possible to meet domain-specific needs. Reusing the same security standards across different communication protocols supports the interoperability of these protocols.
Correlations between Protocols and IEC 62351 Cybersecurity Standards
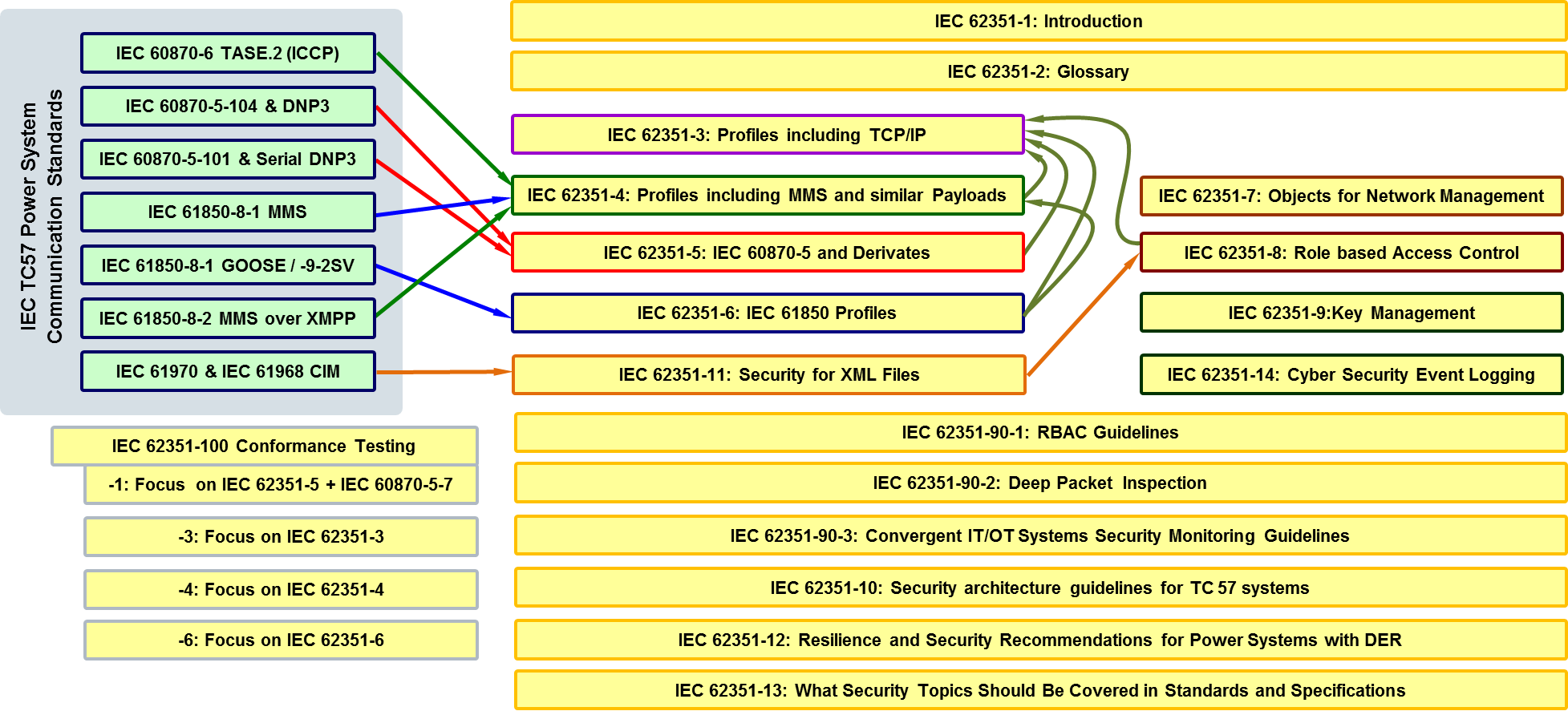
Key IEC 62351 Cybersecurity Standards for TC57 Protocols
IEC/TS 62351-1: Introduction: This first part of the standard covers the background on security for power system operations, and introductory information on the series of IEC 62351 security standards.
IEC/TS 62351-2: Glossary of Terms: This part includes the definition of terms and acronyms used in the IEC 62351 standards. These definitions are based on existing security and communications industry standard definitions as much as possible, given that security terms are widely used in other industries as well as in the power system industry. The terms in this glossary are provided for free access on the IEC web site at http://std.iec.ch/terms/terms.nsf/ByPub?OpenView&Count=-1&RestrictToCategory=IEC%2062351-2
IEC 62351-3: Data and Communication Security – Profiles Including TCP/IP. These security standards cover those profiles used by:
– IEC 60870-6 (TASE.2 / ICCP)
– IEC 60870-5 Part 104
– IEEE 1815 (DNP 3) over TCP/IP
– IEC 61850 over TCP/IP
IEC 62351-4: Data and Communication Security – Profiles Including MMS and Similar Payloads. These security standards cover those profiles used by:
– IEC 60870-6 (TASE.2 / ICCP) using MMS
– IEC 61850-8-1 using the MMS profile of data objects
– IEC 61850-8-2 using XML XSDs mapped from MMS data objects
IEC 62351-5: Data and Communication Security – Security for IEC 60870-5 and Derivatives (i.e. DNP 3.0). These security standards cover both serial and networked profiles used by:
– IEC 60870-5-7 (security details for IEC 60870-5-101 and 104)
– IEEE 1815 (DNP 3)
IEC 62351-6: Data and Communication Security – Security for IEC 61850 Peer-to-Peer Profiles. These security standards cover profiles in:
– IEC 61850 that do not run over TCP/IP – GOOSE and SV
Additional IEC 62351 Cybersecurity Standards and Technical Reports
IEC 62351-7: Network and System Management (NSM) of the information infrastructure, which defines abstract NSM data objects for the power system operational environment and reflects what information is needed to manage the information infrastructure as reliably as the power system infrastructure is managed. A mapping to SNMP MIBs was also developed and is available as code components.
IEC 62351-8: Role-Based Access Control for Power System Management. The purpose of this standard is to:
– Introduce “subjects-roles-rights” as authorization concept (in ANSI INCITS 359-2004, referred to as “users-roles-permissions”)
– Promote role-based access control for the entire pyramid in power system management
– Enable interoperability in the multi-vendor environment of the power industry
– IEC 61850-90-19 is developing the RBAC requirements for IEC 61850.
IEC 62351-9: Key Management. This standard specifies how to generate, distribute, revoke, and handle digital certificates and cryptographic keys to protect digital data and its communication. Included in the scope is the handling of asymmetric keys (e.g. private keys and X.509 certificates), as well as symmetric keys (e.g. session keys).
IEC/TR 62351-10: Security Architecture. This technical report targets the description of security architecture guidelines for power systems based on essential security controls, i.e., on security-related components and functions and their interaction.
IEC 62351-11: Security for XML Files. This standard defines the security requirements for exchanges of XML-based documents which are used for IEC 61970 as well as for some types of information exchanges in IEC 61850.
IEC/TR 62351-12: Resilience for Power Systems with DER Systems. This technical report provides resiliency recommendations for engineering/operational strategies and cybersecurity techniques that are applied to Distributed Energy Resources (DER) systems. It covers the resilience requirements for the many different stakeholders of these dispersed cyber-physical generation and storage devices, with the goal of enhancing the safety, reliability, power quality, and other operational aspects of power systems, particularly those with high penetrations of DER systems.
IEC/TR 62351-13: What Security Topics Should Be Covered in Standards and Specifications. This technical report provides guidelines whose purpose is to support the developers of standards with addressing cybersecurity at the appropriate level for their standard. This document provides suggestions on what security topics should be covered in standards and specifications that are to be used in the power industry, and was a major source of information for IEC Guide 120, “Security Aspects – Guidelines for their Inclusion into Publications”.
IEC 62351-14: Cybersecurity Event Logging. This part of the IEC 62351 series specifies technical details for the implementation of security logs: communication, content and semantics.
IEC 62351 Cybersecurity Conformance Testing Specifications
IEC 62351-100-1: Conformance Testing for Part 5: IEC 60870-5-7 and DNP3
IEC 62351-100-3: TLS Conformance Testing for Part 3
IEC 62351-100-4: MMS Conformance Testing for Part 4
IEC 62351-100-6: Conformance Testing for IEC 61850-8-2 and IEC 61850-9-1
IEC 62351-100-7: Conformance Testing for Network Management*
IEC 62351-100-8-1: Conformance Testing for Role-Based Access Control*
IEC 62351-100-8-2: Role-Based Access Control for 61850 in 90-19*
IEC 62351-100-9: Conformance testing for key management*
IEC 62351-100-14: Conformance testing for Event Logging*
*Pending
Role of IEC 62351 with Respect to Other Cybersecurity Standards